
In this blog post, I will be providing a comprehensive rundown on private proxies — what is it, the advantages of using private proxies, and a brief overview of its different types.
The goal is for you to gain a better understanding of proxies and how they can effectively aid in some of your vital business processes.
Most people already have a vague understanding of proxies and how they work, but not everyone knows that proxies are indispensable business tools.
Let’s dive right in, shall we?
Post Quick Links
Jump straight to the section of the post you want to read:
WHAT IS A PRIVATE PROXY?
In case you don’t know what a proxy is yet, think of it as a middleman or intermediary between your company’s devices and the web servers you want to access. I tackled this on a separate blog where you will learn in detail what proxies are and how they work.
You need a middleman for several reasons, one of which is for your identity to be hidden from the destination web server.
Let’s say that you have an e-commerce business that sells beauty products. To know if the way you priced your products are consistent with market pricing, you need to visit competitor websites and look at their products and prices.
Now, you wouldn’t want your fiercest competitors to know that you’re snooping, right? This is where proxy servers come in handy. The proxy sends the requests on your behalf using its credentials (i.e. IP address).
There are several types of proxies, but what we are tackling here are private proxies. It’s important to keep these in mind when talking about private proxies:
- Paid proxies: When we talk about private proxies, we are referring to proxies that require authentication as opposed to public and free proxies.
- Anonymous proxies: We are also referring to private anonymous proxies, not those transparent ones that do not change your IP address and therefore do not provide privacy.
Transparent proxies have a different purpose too since they are mostly used to authenticate users on wireless networks and to enforce traffic restrictions.
Private proxies are maintained by companies and they, therefore, come with a price tag. And I should say outright that business-to-business organizations should use private proxies and steer clear from free ones.
WHY SHOULD YOU AVOID PUBLIC PROXIES?
You may be wondering: Why can’t you use public proxies? They help you save money and does the same job as private proxies, so why not?
If you’ve been in business long enough, you probably have realized (and may have learned the hard way) that free business tools are often laden with hidden disadvantages that in the end, can cost you more.
Christian Hascheck, owner and developer of Proxy Checker, ran a massive scan on 25,443 free proxies and found that only 14% of them were “good” or safe proxies.
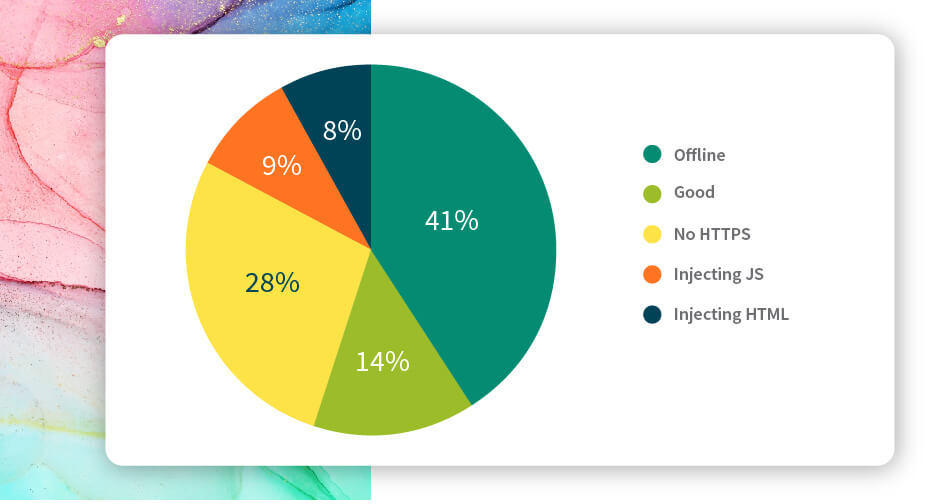
This image is taken from Christian Hascheck’s blog where he analyzed 25,443 free proxies and found only 14% of them to be safe.
28% block HTTPS traffic, 9% are injecting JS, 8% are injecting HTML, while 41% were offline at the time of his testing. Now, this may not look like much at first glance. After all, only less than 10% are injecting HTML and JS, respectively.
But when you look at the raw data, that’s when red flags go off.
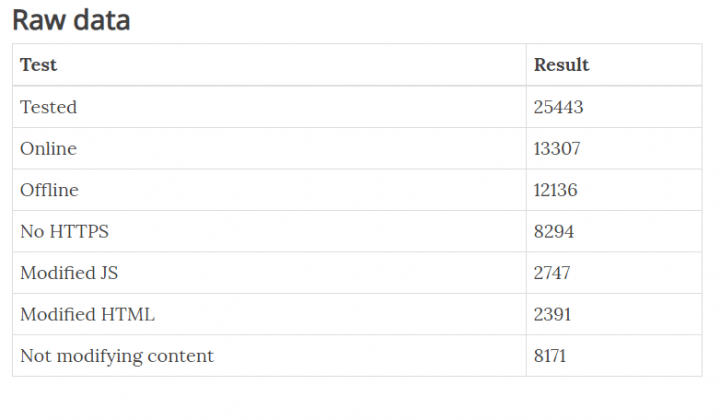
This screenshot of a table is still from Christian Hascheck’s blog. It presents the raw data where he scanned over 25,000 free proxies.
The raw data reveals that only 8,171 free proxies do not modify the content, although this doesn’t mean that they are completely safe to use.
The only way to use proxies safely is when they allow HTTPS traffic. The fact 8,294 of free proxies were found to ban HTTP traffic raises some concerns.
They could be allowing HTTP traffic only because they want to see your traffic, analyze your data, and in the process get hold of sensitive information like usernames and passwords.
For companies, using a free proxy can result in giving the people behind them free reign on company databases and confidential information. Specifically, here are some disadvantages of using free proxies:
- They can contain malware and viruses.
- They can monitor your online connection and activities.
- They can get hold of your login cookies.
- They are very slow.
There could still be a few free proxies that you can use securely, but how can you distinguish them among the tens of thousands that aren’t safe? You simply can’t, so the safest way to go is to use private proxies.
WHY SHOULD B2B COMPANIES USE PRIVATE PROXIES?
Now that you know that free proxies are generally not safe to use, you should also learn about the advantages of using private proxies. What benefits do they give to companies?
To make things simpler, I divided the section into two — benefits of proxy servers to an organization’s overall security and the overall network infrastructure.
BENEFITS TO OVERALL SECURITY
Cybercrimes are becoming rampant. And the victims are not only individuals or even large companies, but the majority of the victims are small business organizations. This was what Verizon’s 2019 Data Breach Investigations Report found out.
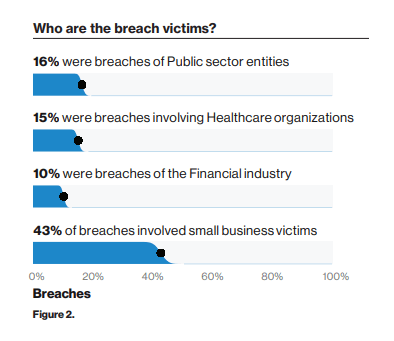
This graph shows the percentage of data breach victims according to Verizon’s 2019 DBIR. 16% were public sector entities, 15% were in the healthcare industry, 10% belonged to the financial sector, while 43% were small businesses.
Among the victims of data breaches, 43% are small businesses. Maybe this can be traced to the fact that most small businesses think that they aren’t being targeted.
Small businesses are also more focused on “cost savings and productivity improvements” rather than focusing on the security and management of their information. This is according to a research study conducted by AIM (Association of Image and Information Management).
In today’s internet-driven world, however, I believe that everyone is a target of these cyber crimes and everyone must take proper measures.
Additional layers of security like using proxy servers must be explored to avoid being victimized by cybercriminals. Proxy servers are widely known to mask your IP credentials so that those who are snooping will only see the proxy IP address and not your real IP.
Masking your IP address is an important function of proxy servers since your IP can reveal a lot of things about you and your company. The tweet below says it all:
https://twitter.com/limeproxies/status/1156059139652689920
Because of how proxies work, they effectively help companies reduce the risk of data breaches and help them perform vital tasks anonymously.
Reduce the risk of data breaches. Since the proxy server is the one sending the requests on your behalf using the proxy IP and credentials, it acts as a shield between you and the cyber criminals lurking behind, waiting for an opportunity to pounce.
Hackers may still find a way to get into the proxy, but they will find it very difficult to break into your company databases or servers which contains all your sensitive data. Without a proxy, hackers will dive right into your servers.
Using a proxy server adds another layer of security for your company, making it difficult for hackers and cybercriminals to steal user information.
Perform activities anonymously. Proxy servers also act as an anonymizing agent since they hide the identity of its users. While others take this feature lightly by using proxies as a way to access restricted entertainment content, businesses should know its importance.
Put into perspective, the ability to be anonymous through the use of proxy servers enable company whistleblowers and news reporters to protect themselves and their confidential sources, respectively.
Security offers are also able to secure the privacy of business partners and clients with the use of private proxies.
BENEFITS TO THE OVERALL NETWORK INFRASTRUCTURE
Protecting your company and its resources (both information and human resources) is not the only function of private proxies. These proxy servers also do wonders in the overall network infrastructure of your organization.
Let’s take a look at what they can do for you:
- Increase speeds: Proxy servers can cache web pages and files, making subsequent requests to the same files a lot faster. They can also compress traffic and get rid of website ads that make a page load longer.
This is the very premise behind the development of the iTiva video content delivery solutions, and other content delivery networks.
The CTO of the now-defunct digital media company said this statement in an interview:
“Having seen that there were problems with servers and problems with peers, we asked if there other sources of bandwidth we could use. The answer was yes, every corporation and many ISPs are installing proxy servers. A proxy server saves a copy of everything it sends, so it can reduce the cost of bandwidth if more than one person uses it.”
Proxy servers are a crucial business tool as it allows companies to improve connection speeds and save on bandwidth.
- Balance web traffic: When your website gets a huge amount of traffic, there’s a chance that your web server will crash. This will result in people getting 404-page results, which will affect their brand loyalty and ultimately your sales.
Website crashes also negatively affect search results ranking. Even websites that are slow to load are affected in the same way.
Did you know that a Google study found out that users who experience even just a 200-millisecond latency tend to search less frequently?
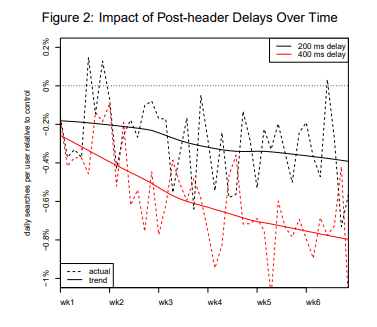
This graph from Google shows the decreasing trend in daily searches for users who experienced 200 ms and 400 ms delays.
Essentially, what Google was trying to establish in their experiment is that website speed matters as users do fewer searches the longer they are exposed to delay.
Along with cloud storage and peering, proxy servers can help your website reach its optimum speed. The proxy server works in two ways:
First, it is used to create a web address that will be the sole access point of the website. This eliminates the need for visitors to use different IPs to access the website.
Second, the proxy server balances the requests and distributes them equally to web servers so there won’t be an overload.
- Control and monitor employee internet usage: Every company has internet usage policies in place to enhance employee productivity. These policies involve usage restrictions such as inappropriate websites and social media platforms.
With the use of proxy servers, network administrators can easily implement these restrictions.
They can block employees from accessing restricted websites, and can even log the sites being accessed to ensure adherence to the policy.
Security officers also use proxy servers to monitor and detect data breaches and other illegal activities that network users might be involved in.
WHAT ARE THE TYPES OF PRIVATE PROXY IPS?
Now that we have established that private proxies are indeed beneficial to your company in terms of overall security and improving network infrastructure, you might be getting ready to buy some.
Before you do that though, there’s still something you need to know which can help you choose a proxy provider.
Let’s briefly discuss the different types of private proxy IP addresses first.
#1 PRIVATE DATACENTER PROXIES
Let’s start with datacenter proxies which are the most practical and the best fit for businesses. They are also the most common proxy IP and they are maintained by data center servers.
They don’t have anything to do with your ISP and they are typically purchased in bulk so you will have a pool of IP addresses.
The most practical choice is the datacenter proxy IPs. They are cheaper than the other two IP address types (to be discussed below), but all the same, they can give you the same results.
Besides, datacenter IPs saves you from legal predicaments surrounding the privacy of the IP owner as you don’t need anyone else’s permission to use them, just the data center that’s maintaining these IPs.
#2 PRIVATE RESIDENTIAL PROXIES
From its name, we can deduce that residential IPs are those that are assigned to residential homes. These are managed and distributed by Internet Service Providers or ISPs. Residential proxies are more expensive because they are relatively difficult to obtain since they are already owned by home.
The use of residential proxy IP addresses is also questionable especially when the owner of the IP does not know that you are using their home network as a proxy. As a company, residential IPs are not advisable since they can pose legal issues.
#3 PRIVATE MOBILE PROXIES
Private mobile proxies involve the IP addresses of mobile devices, which are managed by mobile network providers. Mobile IPs are also difficult to obtain just like residential IPs, and they can be very expensive.
Privacy concerns also surround the use of mobile proxies since there is no assurance that the mobile device owner is explicitly aware or approved of you using his or her GSM network.
BUSINESS USE CASES OF PRIVATE PROXIES

Private proxies are being used by companies in different business processes. Here are some of the most popular use cases of private proxies in business organizations.
#1 CONTENT CURATION
In a previous blog post, I have the following definition of content curation:
“Content curation is when you pick out the best and most applicable content on the web and present them to your readers in an organized manner, based on a specific topic.”
The process of pooling web content is long and tedious, something that is best done with the use of automation tools.
With the right tools, you can gather relevant, topic-based content in a fast and accurate manner. But these tools need to be protected by a private proxy so they won’t easily get blocked by websites that have strict security measures.
For this reason, agencies and website owners that do content curation use proxy servers. And we’re not talking about just a few companies. In a research study by Curata, it was revealed that 48% of companies curate their content regularly.
To break this percentage down, we have:
- 16% of companies that curate content daily
- 13% of companies that curate content three times a week
- 19% of companies that curate content once a week
- 17% of companies that curate content monthly
- Over 20% of companies that curate content quarterly or less frequently
- 12% of companies that never do content curation
#2 COMPETITIVE PRICE MONITORING
Competitive price monitoring is an essential business process that enables companies (particularly e-commerce businesses) to implement an effective pricing strategy.
It is an age-old strategy that requires companies to browse the aisle of their competitors’ stores so they can check out the latest prices. With the advent of the internet and technology, competitive price monitoring is taken to a different level.
Every company that wants to be successful in their business ventures need to have a price intelligence strategy in place, especially since there are hundreds of thousands of online stores. Shopify alone has 800,000 active stores that are using the e-commerce platform.
I have previously determined five steps in starting a price intelligence strategy, and these are:
Step 1: Determine Your Goals
Step 2: Get To Know Your Target Market
Step 3: Identify and Monitor Your Competitors
Step 4: Select a Competitive Pricing Tool to Manage Your Pricing Intelligence Program
Step 5: Decide on a Pricing Strategy Based on Your Price Intelligence Program
The use of a competitive pricing tool signals the need for companies to also use proxy servers as an added layer of protection.
Without proxies, you can’t go far in your price monitoring since competitor websites that are better equipped can immediately blacklist your tool.
Private proxies help make your price intelligence strategy more effective. And with the e-commerce industry being a trillion-dollar industry, you need all the help you can get to thrive and get ahead of the competition.
#3 WEB SCRAPING
Content curation and competitive price monitoring require you to use web scraping software tools that can scrape the web for the information you need.
For content curation, you need a web scraper to gather all relevant content. There are web scraper tools that can even put additional criteria into their parameters, such as social media engagement.
The same thing goes for price monitoring. You need a web scraping tool that scrapes the prices of specific products for you. These are specifically called price monitoring tools, and most of these tools can already manage your product prices for you.
In essence, though, these tools scrape websites for the information you need. While this isn’t inherently wrong since you can also do it manually |(although on a smaller scale), most websites don’t welcome these tools.
They have anti-bot measures that automatically flag and block IP addresses that they suspect of bot-like behaviours. Your countermeasure is to use private proxies along with customizing your tools to imitate human behaviour.
You will learn more details on our Ultimate Guide to proxies for Web Scraping, including:
- Why you need proxies for scraping
- How many proxies you need
- The legal considerations when using proxies
- Web scraping use cases
#4 MULTIPLE ACCOUNTS IN E-COMMERCE AND SOCIAL MEDIA SITES
Aside from price monitoring, another way for e-commerce companies to gain a competitive advantage is to have multiple vendor accounts in e-commerce platforms such as Alibaba and Amazon.
This practice is not illegal and several companies are doing it. However, e-commerce sites might flag you as a vending bot if you don’t use proxies since all of your vendor accounts are using the same single IP address.
By using proxies, you can assign one IP to each vendor account, so you don’t run the risk of getting blacklisted.
Private proxies also help social media managers and affiliate marketers manage multiple accounts on social media platforms.
#5 BIG DATA MINING
In 2017, 53% of companies around the world had started adopting big data as part of their business processes.
This figure has since increased, and in fact, some experts have gone as far as claiming that data is the new oil, as this tweet by Nick Bilodeau, a Financial Technology influencer, suggests:
https://twitter.com/FinMKTG/status/1150728471078932480
Along with this development is the demand for data scientists. Sought after data scientists are those that have specific technical skills such as:
- Big data
- Machine learning
- Apache Hive
- Apache Hadoop
- PIG
- MapReduce
Almost all of these skills are also crucial in developing and managing web scraping tools since these tools are also used in big data mining. Again, proxies play an important defence mechanism against anti-bot measures.
#6 CYBER SECURITY
One of the benefits of private proxies is providing corporate security since it serves as a buffer for cyber attacks. Instead of having direct access to a company’s servers, hackers and DDoS attackers need to go through the proxy server first.
I already mentioned that according to a report by Verizon, almost half of cybercrime victims are small businesses. This only means that small businesses need to beef up their network security by investing in tools such as private proxies.
You’d also be surprised to know that huge global corporations are not immune to these cyber attacks. Here’s a list of some of the greatest data breaches that happened in recent years:
Company Name
(with links to the news source)
Year of Attack Number of Hacked Accounts
Marriott 2014 to 2018 500 million
Under Armor February 2018 50 million
MyHeritage October 2017 92 million
Facebook July 2017 50 million
Equifax September 2017 145.5 million
Uber October 2016 57 million
Adult FriendFinder October 2016 412 million
MySpace May 2016 360 million
Think of the number customers affected by these data breaches and how they affected their brand loyalty.
Imagine the millions of dollars these companies had to spend to mitigate the damage, and the millions of potential sales lost because people had lost their confidence in the company.
Before this worst-case scenario happens to your company, it’s better to be proactive in cybersecurity and employ tools to keep these attacks away. It’s also a best practice to keep up with the latest news about cybersecurity as cybercriminal will always find a way to challenge even the most top of the line security tool.
#7 SEO RESEARCH & REPORTING
Whether it’s keyword research or rank tracking, SEO automation tools are being used predominantly since they are faster, more inclusive, and a lot more accurate compared to manually doing these tasks.
In a separate blog post, I’ve listed some tips in selecting the right rank tracking tool, but they are actually effective in selecting other SEO tools too.
But regardless of the tool you choose, always bear in mind to protect them by using private proxies. Protect them from what? You might ask.
First and foremost, the enemy of these tools are your target websites’ stringent security measures against bots. You also can’t blame them. You might even be using the same level of security for your websites.
We can’t blame you or any websites. After all, 51.8% of web traffic is from bots, which is not alarming in and of itself. But then, 28.9% of this bot web traffic is from bad bots!
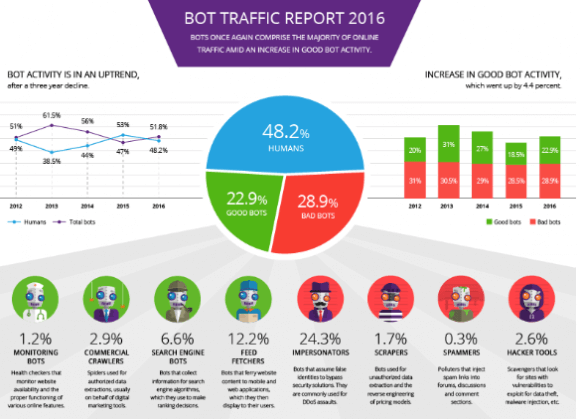
This infographic from Imperva breaks down the web traffic by percentage. 48.2% are from humans, 2.9% are from good bots, while 28.9% are from bad bots.


About the author
Rachael Chapman
A Complete Gamer and a Tech Geek. Brings out all her thoughts and Love in Writing Techie Blogs.
Related Articles
5 Tips When Using a Bot To Avoid Proxy Blocks
Your choice of proxies is another factor to carefully consider before you get into the scraping proper. While all proxies offer you anonymity, some are careful and more difficult to detect than others.
The Ultimate AdWords Retargeting Guide
Google AdWords is much complicated if you don’t understand how to use it properly. It is not just about gaining eyeballs online for clicks rather, it can be used for ‘retargeting’ as well.