
QUICK LINKS:
What is an IP address?
If you exist in the digital world, there is no doubt that you have come across the term “IP address.” But again not all of us are technicians, so some probably don’t have much knowledge of what an IP address is and how it works.
An IP address is a fascinating numeric number of the modern computer technology created to allow your personal computer to communicate with others over the internet. Billions of digital devices locations are differentiated by an IP address in the same sense someone needs your physical address to send you letters. For a remote computer to communicate with other computers,it requires an IP address.

IP stands for internet protocol. But what does that means? Internet protocols are set of rules and regulations governing all internet activities and World Wide Web actions. Therefore, a standard definition of an IP address is “a systematically laid out interconnecting grid that manages online communication by initiating devices and internet destination, creating a two-way communication.”
Here’s an example of how an IP address looks like 12.345.0.678. These set of four numbers separated by a dot are the key you need to send and receive information over your internet connections.
An IP address is either static or dynamic. Static IP addresses never change, meaning they serve as permanent IP and allows a reliable and straightforward route for remote computers to contact each other. Static IPs carries information regarding the internet service provider of that computer and the continent, country, and the city where that computer is located. Dynamic IP addresses, on the other hand, are temporary assigned IPs each time a computer joins a network. They are generally borrowed from a pool of IPs that is shared by a network of computers.
How are IP addresses assigned?
Given that each IP address must be unique for every computer that is connected to the internet, how are these addresses assigned to every computer? Well, it is a rule for every device that connects to the internet to have its unique IP address. And they are assigned in two ways: dynamic or static. Though there is a trick used for multiple computers to share a single IP address, that is a router.
The internet service provider assigns static IPs, and of course, you are not in a position to configure your PC or any other device manually to respond to a specific address. But in most cases, most folks need to configure their devices. So what can they do to get their own IPs?
By using a Dynamic Host Configuration Protocol (DHCP), your PC broadcast for a unique dynamic IP address to the network. Your internet service provider then responds with an IP address that your PC configures itself with it to use.
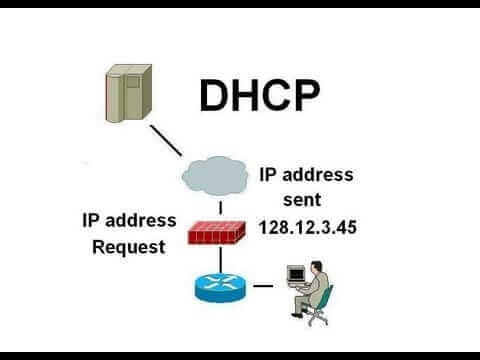
In most cases, static IP addresses are used when your PC needs to be identified by other computers so as they can connect to it. Dynamic assigned IP addresses, on the other hand, are used for private purposes like surfing and read emails.
In the case you have several devices to connect to the internet; you can use a single IP address to identify all of them over the internet. How is this possible? A router, a device with unique IP, acts as a DHCP server between the internet service providers handing out local IPs and your internet devices. As traffic comes in and out of the router, it translates the IP addresses of services to the external unique IP address that it was assigned, and routing the right package of data to the correct device. Hence, the name router came to place.
What is an IP address rotation?
IP rotation is a systematic process of distributing assigned IPs to the right devices randomly or in a configurable manner by an administrator.
When a user connects to her internet service provider, she is assigned an IP address from a pool of IPs. Her internet connection remains with the IP address she was assigned with until a disconnection occurs. And when it happens, the ISP will allocate the user with the next available IP address from the pool thus there will be a transparent IP address rotation process to the user
IP address rotation is observed from outgoing traffic since the source of IP is the primary foundation of all form of internet destinations over internet communications. Rotating IP addresses facilitates the load-balancing between incoming and outgoing traffic as well as distributions of equal resources among role-based control lists.
By rotating IP addresses, the host can avoid all forms of restriction put in place by websites and the government’s censorship programs.
Methods used to rotate IP addresses

- Pre-configured IPs rotation – this technique allows rotation to occur at minutely intervals. After the specified time elapses’, a new IP address is assigned to the user.
- Specific IPs rotation – the internet service provider chooses a new IP address for the outgoing traffic after internet connection is disconnected.
- Random IPs rotation – each and every outgoing connection through the internet service provider is assigned a random rotating IP address.
- Burst IPs rotation – IP addresses are rotated as per the specified number of connections. For instance, if 20 connections are initiated, the 21st will originate from a different IP address.
IPs rotation legitimate users
- ** SEO companies who use the rotation to check for keywords ranking**
- Data warehouse to access wider selection from their localities and destinations
- Amazon, Yahoo, and Google use IP rotation firms to boost their outgoing bots to distribute load of their networks
- Business intelligence companies to mine, harvest or retrieve data for data analysis
- Qualitative and quantitative research companies to observe variations
- Anti-piracy and anti-counterfeiting agencies for researching questionable content and data harvesting
- Corporate firms to eliminate geo targeted presentations
- Private users to surf the internet anonymously
IPs rotation illegitimate users
The most well known widespread of IPs rotation is from hackers, intruders, and spammers. They use IPs rotation to fool the users using mail servers to distribute spam emails to appear like they are originating from different network blocks. Their most prominent mission is to deliver as many mails as possible to have high return rates.
There are reported DDOS attacks when IPs are rotated. However, the engineers of these attacks prefer botnets.
Also Read About: All About Proxies
Why proxies offer better IPs rotations

A website can have your identity by merely looking at the IP address assigned by the internet service provider. However, you can hide your real identity by subscribing to Proxy IP rotation. The good side of proxy rotation is that it assigns you with a new IPs rotation every time you request a webpage. The website can only see the random IP address assigned to your computer and not your real IP address.
Using a well-dedicated proxy IPs rotational service strengthens your connection, and it becomes virtually unbannable. When your IP is continuously refreshing time to time, excessive request blocks are avoided giving you a higher browsing experience than you could get from internet service providers IPs rotations.
A proxy pool consists of millions of IP addresses and therefore allocating random IPs though proxy gateways to set up a fantastic rotation interval. With random fresh proxies IPs, security limits become unnoticeable in the application like scrapebox giving you the best surfing anonymity and privacy.
Learn how to use proxies : A full guide how to use PROXY
Post Quick Links
Jump straight to the section of the post you want to read:


About the author
Expert
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat.
Related Articles
5 Brand Protection Techniques you can Implement today
WQ=hile lead generation and prospects engagement is a priority, keep your brand protection as a priority also. 5 Brand Protection Techniques to Implement
Top 10 Machine Learning Algorithms that will make work simple
It is defined as a scientific study of statistical models, computer systems and algorithms. Learn more about our web scraping proxy service.