
Almost every application that we download to the mobile phone requires access to some of our data. Every activity on the Internet can be observed by companies, ISPs, government, hackers and so on. Pixels track what do we click on, what are we liking and commenting on, what are we doing on a regular basis, and what are we searching for.
With the help of the IP address, the way we navigate the online world can be monitored, which includes the location of a certain address, and other information.
Many times, we unconsciously, give access to our data. All of this may seem overwhelming, but it’s important to be aware of the danger. Most of this information is used to find the target group in a quicker and more efficient way when the ads and creating a better user experience are in question. However, it is still too much for many.
The bigger problem is that, with insufficient consideration, we allow ourselves to be the easier target when it comes to hackers and identity thieves on the network. But fortunately, there are ways how to gain control over your data.
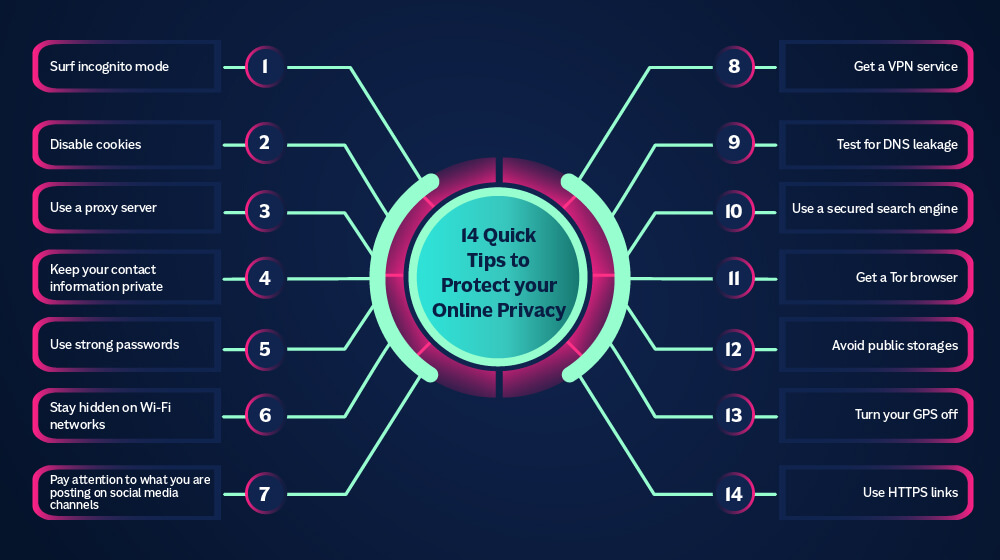
1. SURF INCOGNITO MODE
Search engines can remember your search history, data or cookies, so you can use the incognito window to prevent this.
Incognito mode actually uses a special window for what you are searching for and you can enable it in many browsers, such as Chrome, Mozilla, Opera, Internet Explorer.
For example, when you use Chrome for research you can switch to incognito mode.
To get an incognito window in Chrome:
- Open your Chrome.
- In the upper right corner, click on the three dots.
- Select option New incognito window.
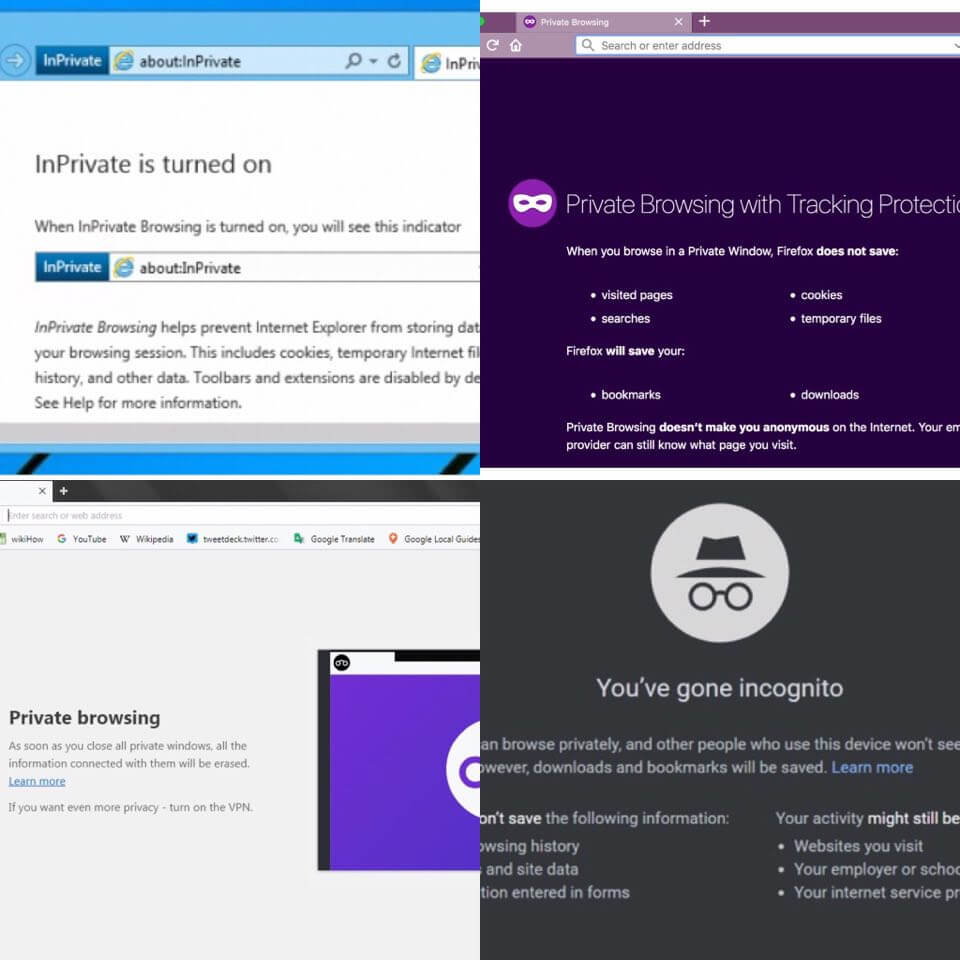
When you want to exit incognito mode, just turn off all the incognito windows that you’ve opened.
Everything you downloaded will be saved even though it was downloaded during the incognito mode.
However, your activity will be visible to the websites you have visited as well as your internet service provider.
Keep in mind, therefore, that your data is protected but not hidden.
2. DISABLE COOKIES
You’ve probably noticed many times that you were using cookies during your visits to some website.
They represent small data collectors and remember the names and codes, what you searched, what you bought, and similar. They follow your browsing activities.
Also, not all cookies are “of the same quality”. Major websites generally use safer cookies, but there are also those which data can be leaked.
Some websites allow you to choose whether you’ll allow access to all cookies or just specific ones.
If you want to be sure when it comes to protecting your data, the best option is to block them completely.
You can block cookies on both mobile devices and computers.
3. USE A PROXY SERVER
By using a proxy server you can also hide your IP address and make your data and internet activities anonymous and secure.
These kinds of servers are also mediators between you and the internet content. They intercept content that needs to reach you and therefore they provide a secure connection.
With the help from a proxy server, you can connect to any other proxy server in the world and access content that is geo-blocked.
VPN service provides more security, but proxy servers are a great option for low-stakes tasks.
However, proxy servers are a great option for low-stakes tasks.
You can try LimeProxies or ShadowSocks.
Limeproxies offers many possibilities such as:
- High performance
- Choice of more than 40 geo-locations
- Changing your proxy IP address on your demand
- Fully automated control panel
4. KEEP YOUR CONTACT INFORMATION PRIVATE
Many companies and brands ask for your email address and phone number, as you’ve probably noticed.
This information is important to them because it enables them to send you queries or emails from time to time in order to get your attention.
However, happens that this contact information ends up being sold and not only kept in the database of the company to which you have entrusted it.
To avoid receiving spam messages, keep your contact information hidden and provide only to the verified brands you want to receive messages and news from.
Creating a separate email address is a good idea. You can use it when you fill in contact forms, and in this way, your messages will not get mixed with, for example, messages related to your business.
5. USE STRONG PASSWORDS
Although it may seem to you that strong passwords are not of great importance, you are wrong.
Today, hackers are more capable than ever.
Use these tips for creating passwords:
- Use at least 12 characters.
- Combine both numbers and upper case and lower case letters.
- Do not use the same password for multiple accounts.
Some websites, such as Gmail, offer the ability to protect your account with the help of the phone number. Take advantage of each of these options in order to keep your privacy while being online.
6. STAY HIDDEN ON WI-FI NETWORKS
Connecting to public Wi-Fies helps you hide your IP address by taking over the address of the place where Wi-Fi is located.
However, it is much more important to emphasize that literally everyone has access to them, and they are easy targets for hackers. So, this option is not overly recommended, but if you really need to connect, be careful.
Do not transmit any important information such as passwords, credit card data and similar information through public Wi-Fi networks.
Also, try not to be connected for too long.
Use a VPN service that will encrypt your information and prevent anyone from reaching it.
7. PAY ATTENTION TO WHAT YOU ARE POSTING ON SOCIAL MEDIA CHANNELS
Nowadays, it is very easy to give someone even more information than it is necessary. At first, it seems interesting to fill everything that social networks such as Facebook suggest but you need to be. People share their addresses, where they are currently located, what they do in their spare time and similar. It should be kept in mind that this data is in the least used for advertising campaigns in order to find the target group as precisely as possible.
So, try to make your profiles as private as possible.
Anything that you put on the Internet, even if you delete it, remains remembered by the apps or browser.
It is a good option that almost every social network, whether it’s Facebook, Google, Twitter, offers the ability to modify your privacy.
For example, on Twitter, you can choose Protected mode and select who can see and retweet your tweets.
8. GET A VPN SERVICE
VPN or Virtual Private Network provides a service which hides your IP address and allows you to surf the Internet through a virtual server. Simultaneously, it hides your online activities from anyone who could be tracking them. This way, you leave your data to neither other websites nor your internet service provider.
By using a VPN that covers up your IP address, you have the ability to access websites whose content has been blocked for your geographic area up to that point. The visible address is the one assigned to you by the VPN service, while your real IP address is hidden. The visible one provides you protection for your data, and all internet traffic stays encrypted.
If you opt for this way of maintaining your internet privacy, there are several options to get a VPN service:
- You can set up your own VPN, but this is not a very simple process.
- You can set up your own home VPN, but it will not work properly if you're really at home at that moment.
- You can get a service from a verified VPN provider.
The third option is also the best one. It represents a very fast and simple process.
It takes a couple of minutes to set up a VPN client, connect to it, and your IP address will be changed, and with it, your activity and location will be hidden.
We recommend that you try out services such as Limevpn, ExpressVPN or NordVPN.
Source: Dribbble
9. TEST FOR DNS LEAKAGE
Even though you use a VPN, you can still leave behind some of your information through your DNS traffic.
DNS converts a web address to the IP address that your computer understands. If information about this process gets discovered, information about your behaviour on the Internet can be discovered too.
To check if a leak has occurred, you can try the DNS leak test.
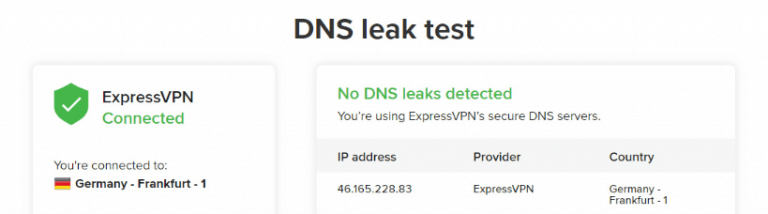
Source: Addictive tips
DNS leak test will inform you if there are any leaks detected.
10. USE A SECURED SEARCH ENGINE
Privacy-focused search engines work differently from the major search engines such as Google, Yahoo, and so on. Secured search engines do not track your information like others who are trying to collect everything they can do, but they are trying to preserve your privacy as much as possible.
If you do not want your information to be sold to advertising companies, you can try DuckDuckGo or Search Encrypt.
11. GET A TOR BROWSER
Tor represents the abbreviation for "The onion router". It is a software that allows you to do everything on the Internet anonymously. Whether it's research, shopping or communication with people with restricted internet access. Just like a VPN client, it covers up your IP address with another address.
Tor browser consists of three layers that compose proxy servers. Because of this layering, it has a metaphorical onion name. When you make any kind of request on the Internet, it passes through the network of Tor network servers. Tor prevents anyone from seeing that the request, in fact, originated from you. This request moves from one proxy server to the other through the layers before it reaches the website that is actually a target destination.
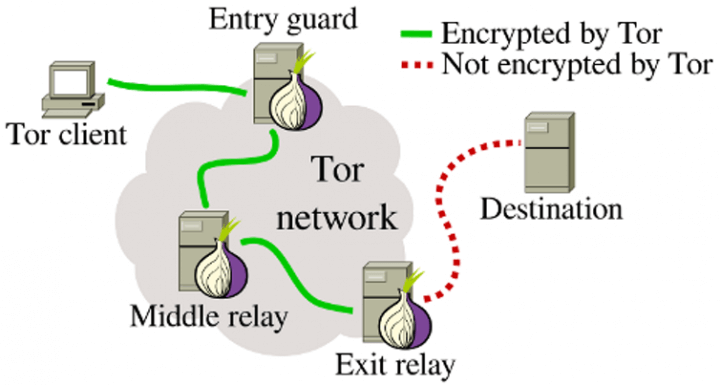
Source: The Conversation
12. AVOID PUBLIC STORAGES
If you do not want to share your private information with everyone, avoid storage in programs such as Google Drive or Dropbox. It could be used or monitored for other purposes
They generally are a great option for storing information and sharing between multiple devices and users.
But, confidential information such as, for example, scanned passports, codes and similar, should never be found in these places.
13. TURN YOUR GPS OFF
By turning your GPS off you will prevent everyone from knowing where you are.
Many applications when downloading to your device require different permissions, and those include access to your location.
When using it is not necessary, turn your GPS off because that way, they will not be able to read where you are.
Some of those applications, such as social media applications, will set up your location online.
Turning the GPS off prevents geotagging, and you certainly do not want everyone to follow your every step.
14. USE HTTPS LINKS
HTTPS stands for hypertext transfer protocol secure.
It is important that the websites you visit contain this abbreviation as part of their address because it indicates the safest connection.
If the website contains only HTTP or BGP and similar, it is not safe enough.
Websites without HTTPS may have malware installed by cybercriminals who can use your data for different purposes.
HTTPS prevents the possibility of someone with bad intentions like hackers or identity thieves to be involved in your online activities.
THE BOTTOM LINE
We'll be honest with you, in the 21st century, it's very difficult to keep your internet privacy. But luckily, as you can see above, there are many ways in which you can prevent someone from coming into possession of your data or following what you're doing.
Of course, being online is our decision. Although it brings significant benefits, it also has its own drawbacks. So be careful of what you share with others and pay attention to keeping as much information as you can to yourself.
Limeproxies, a highly anonymous proxy server with 25 IP addresses* at a time can protect your data. Use the above ways to maintain your internet privacy and it will significantly prevent your personal information from reaching those who could take advantage of you.


About the author
Rachael Chapman
A Complete Gamer and a Tech Geek. Brings out all her thoughts and Love in Writing Techie Blogs.
Related Articles
Why Is It Important to Analyze Competitors’ Prices in Online Stores?
The growth of ecommerce means lots of opportunities for business owners like you. Know why Is It Important to Analyze Competitors’ Prices in Online Stores.
Everything You Need to Know About Private Proxies For Businesses (B2B)
In this blog post, we will be providing a comprehensive rundown on private proxies. Everything You Need to Know About Private Proxies For Businesses